Kindoo Software Releases
▼v.6.0.3 Latest
30-12-2025▼v.6.0.2
04-12-2025Bulk user invitations now support adding users as temporary users.
Suspicious User Activity Detection
We have introduced a new feature that enhances the visibility and control over user Suspicious User Activity. This feature helps identify users who access entry points within a site from multiple recurring devices, which may indicate irregular or risky behavior.
Example
- User opens a door within site S using Device A
- The same user opens a door within the same site S using Device B
- Then the same user opens a door within the same site S using Device A
This pattern will automatically flag the user as suspicious.
Where to Access This Feature
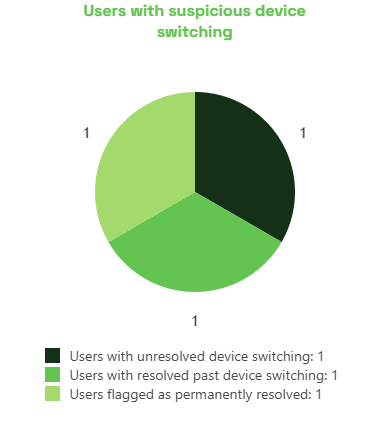
You can access the Suspicious User Detection section directly from the site dashboard. It will appear as a chart titled “Users with suspicious device switching”, which gives an overview of users who may require attention.
Understanding the Suspicious Users Chart
In the Suspicious Users section, you will find a dedicated chart specifically designed to highlight user device-switching behavior. This chart is divided into three categories:
- Users with unresolved device switching
- Users with resolved past device switching
- Users flagged as permanently resolved
You can access more details about the users by clicking on a segment of the chart or the corresponding label in the legend.
Next to each user you will see these action buttons:
- Remove User
- Check Logs
- View details
- Resolve (only available for users with unresolved device switching)
Additionally, you can export the user(s) data to a CSV file for further analysis or reporting.
For users in the resolved or permanently resolved categories, the Resolve button will not appear, but you can still check their logs.
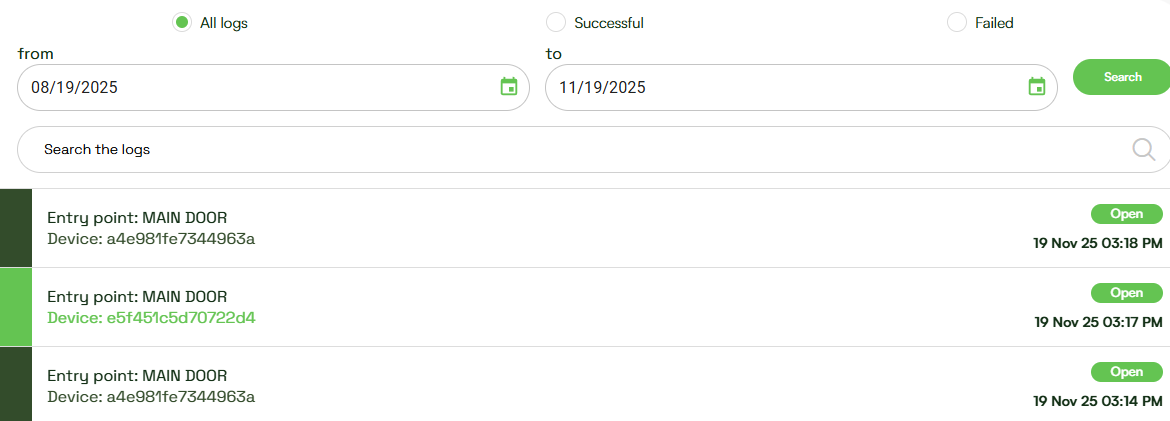
Inside the logs, each device used by a user is displayed in a different color, making it easy to understand access patterns and device-switching behavior. You can also export the user’s logs to a CSV file for further analysis or reporting.
Viewing User Details
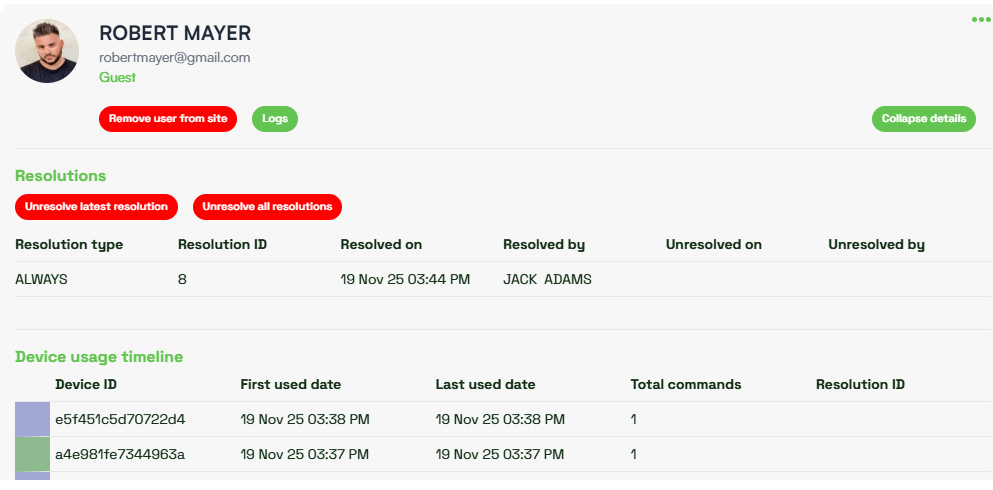
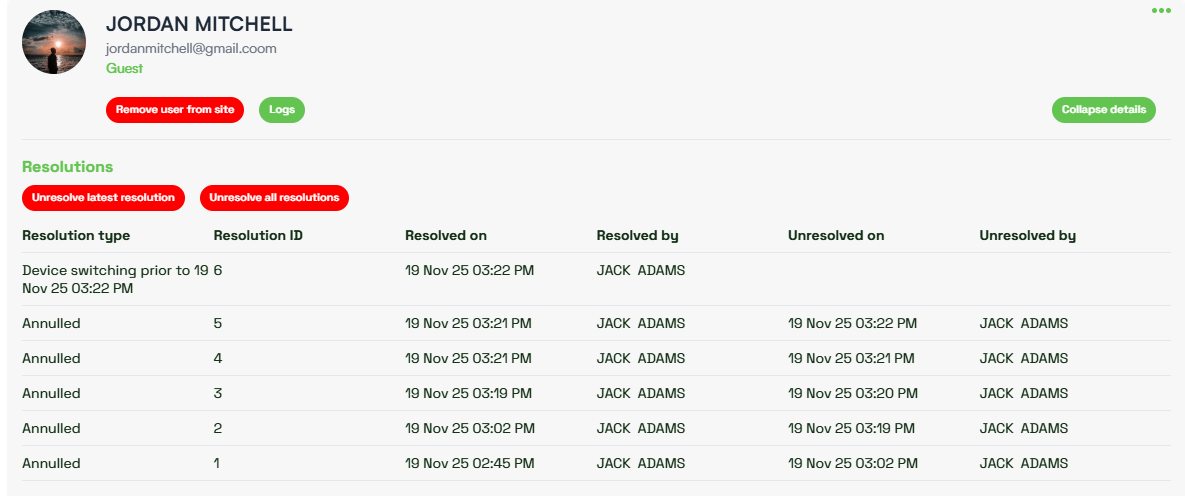
When you click on the View Details for a given user, the following information will be displayed:
- Resolutions – Shows the history of resolutions applied to the user, including type, who resolved or unresolved them, and dates.
- Device Usage Timeline – Displays the user’s device activity, each device is represented by a color, first and last use dates, total commands, and which resolution each device is associated with.
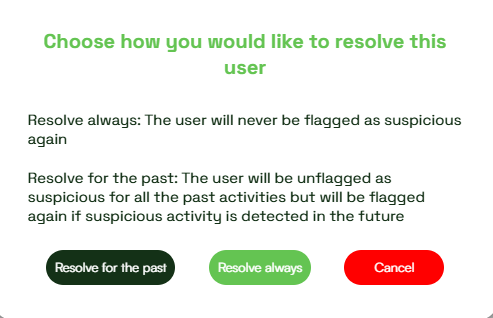
Resolving Suspicious Users (Can be done only by Admins)
Admins can resolve suspicious users in two ways, after entering the “Users with unresolved device switching” segment of the chart (or selecting its corresponding color in the legend):
- Resolve always – Permanently resolves the user. They will never be flagged again.
- Resolve for the past – Temporarily resolves the user. If they repeat the switching pattern (A → B → A), they will be flagged again.
After resolving users, the “Users with suspicious device switching” chart updates automatically to reflect the current status of unresolved, temporarily resolved, and permanently resolved users.
Unresolving Users (Can be done only by Admins)
Admins can also reverse a previous resolution. To do this, go to the “Users with resolved past device switching” or “Users flagged as permanently resolved” segments in the chart, and click on a user to view details. There are two types of unresolve actions:
-
Unresolve Latest Resolution
- Reverts only the most recent resolution applied to the user.
- Previous resolutions (if any) remain intact.
- The user may become suspicious again if their device-switching pattern meets the criteria.
-
Unresolve All Resolutions
- Clears all resolutions for the user, including temporary and permanent ones.
- The user will be fully treated as unresolved and will appear in the “Users with unresolved device switching” category again.
After unresolving users, the “Users with suspicious device switching” chart updates automatically to reflect the current status of unresolved, temporarily resolved, and permanently resolved users.
Automatic Background Scanning & Alerts Process
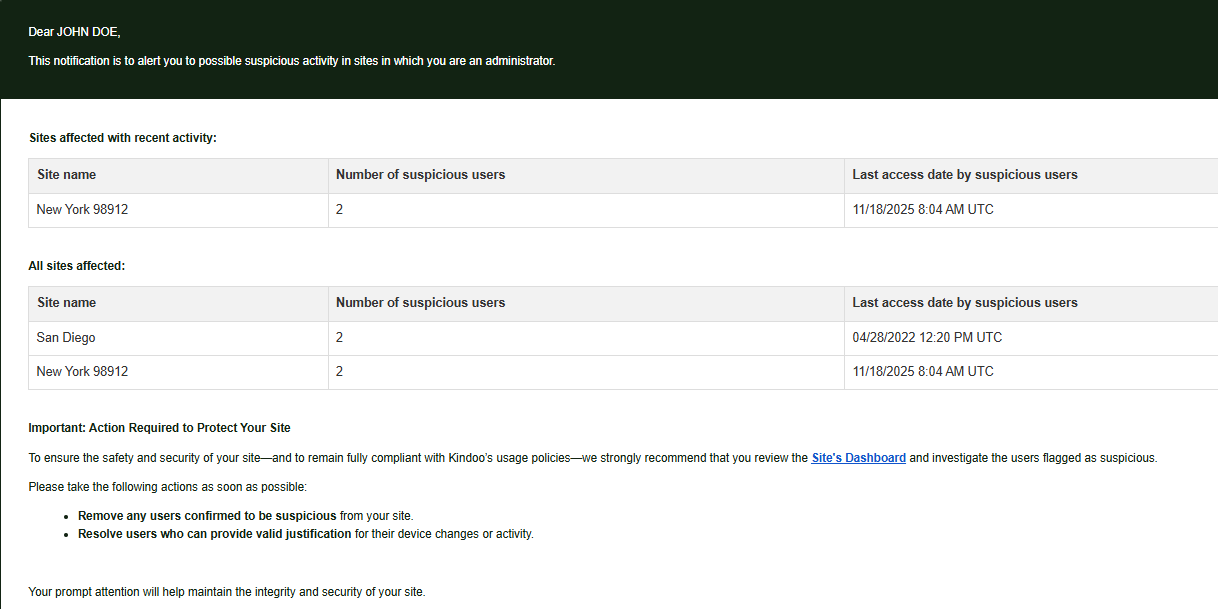
Kindoo now runs a background scan every 24 hours to detect users with recent suspicious activity.
If any suspicious activity is detected within the past 48 hours, the system will send an email to the site admins.
Any Kindoo user that is an admin of 1 or multiple sites in Kindoo will receive at most 1 email per day relating to suspicious behaviors. This email will include a recap of all their sites that have suspicious users that are unresolved with last access date and total number of suspicious users in each site.
▼v.6.0.1
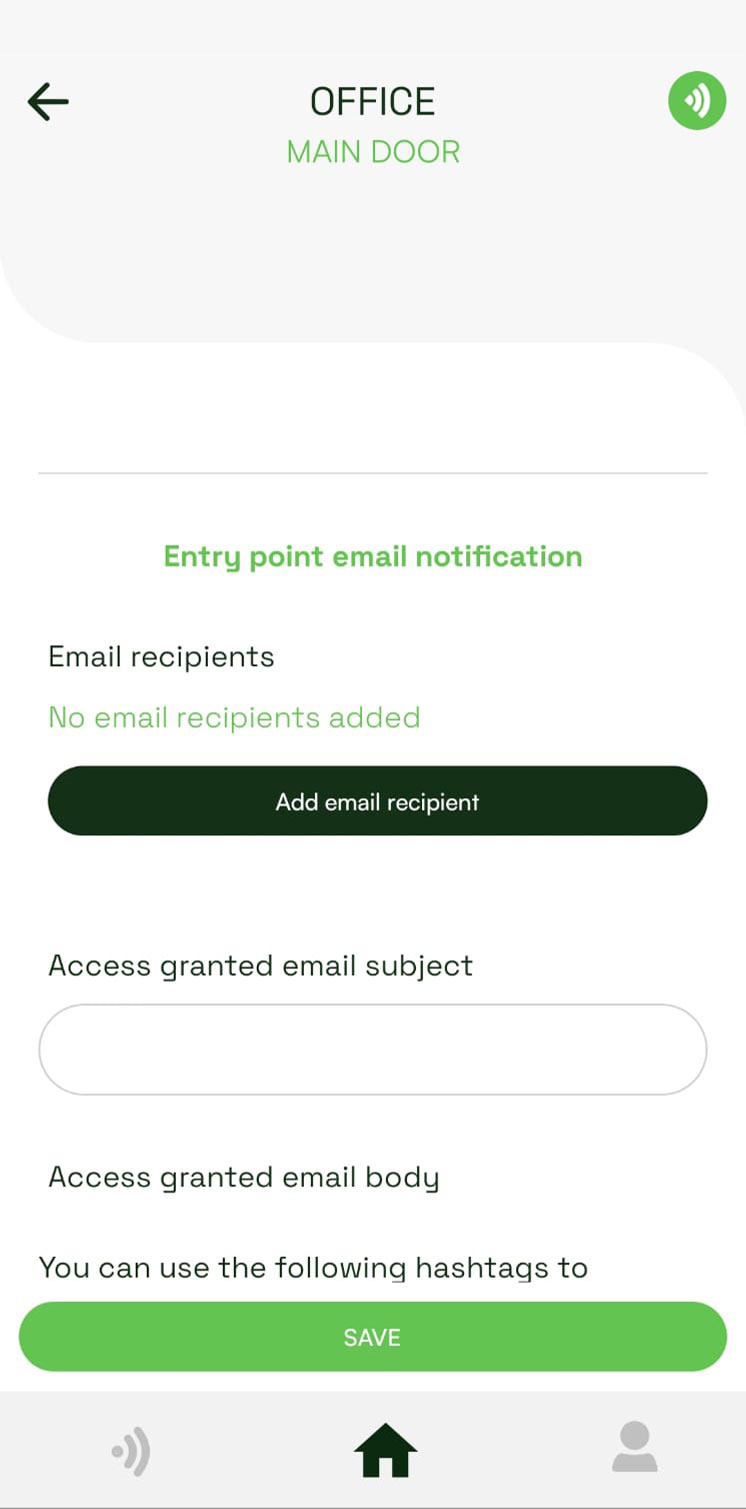
24-10-2025In the Entry Point settings, you can now enable event notification by email that will be sent out to a list of recipients (limit 5). The body and subject of the notification email can be customized for the Access Granted and Access Denied events.
When issuing a command to an entry point, a validation step is now added that will notify the user if the command emitted by the phone reached the entry point recommending to get closer to the entry point in case of failure.
▼v.5.5.4
19-05-2025Users bulk upload edits the user information if the user already exists in the site. In addition, a switch button is now available to choose if the bulk upload should replace the access rights of an existing user or simply add new access rights to the previous existing access rights of the user.
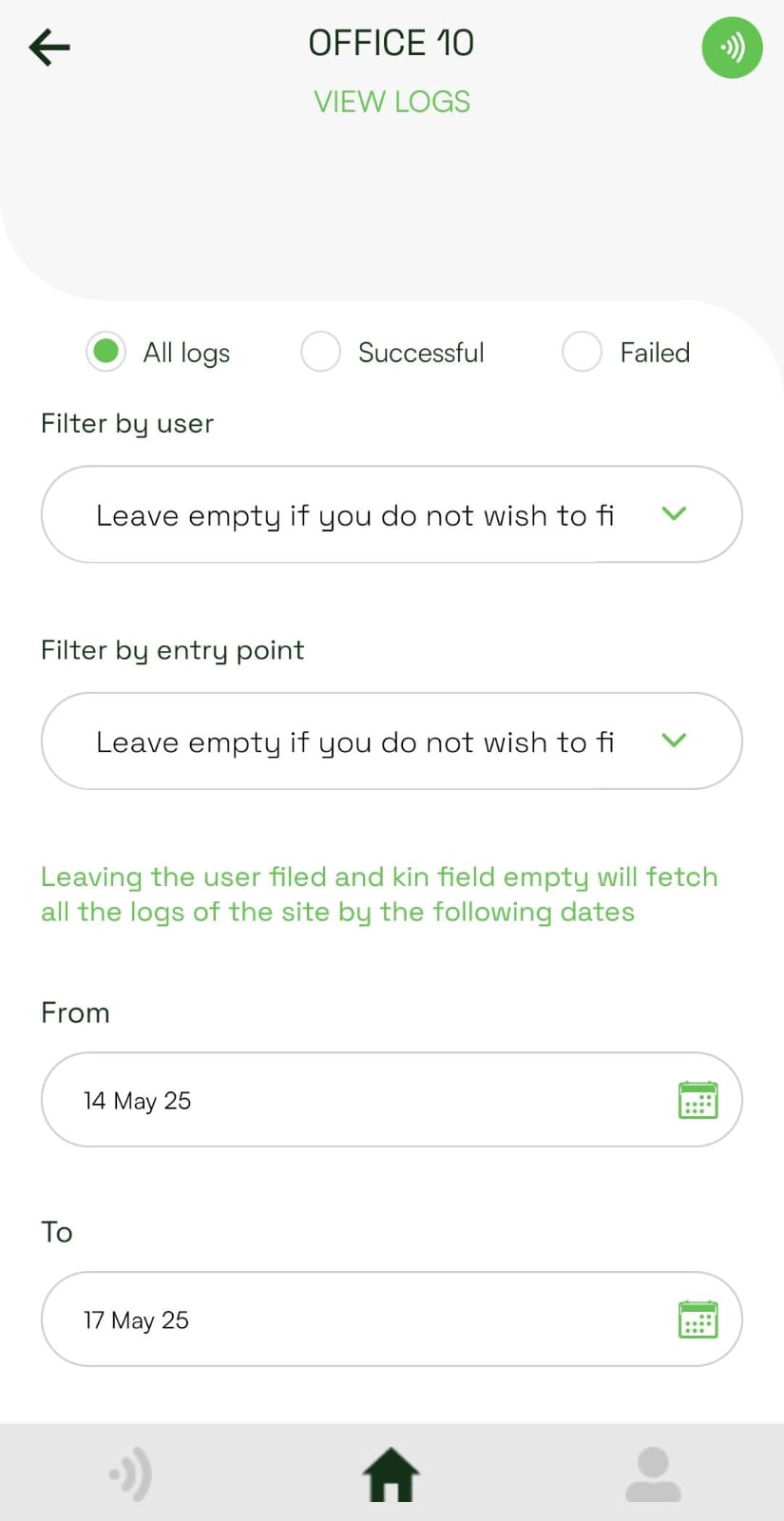
In the access logs view, we added 3 radio buttons (All logs, Successful, Failed). Only one can be selected at a time. The logs will be filtered according to the selected radio button.
When pressing on a log of a user not existing in the site, a modal popup will show the user profile picture, full name and email address. If the user account has been deleted from Kindoo, you will receive an alert that the profile has been deleted.
When pressing on a log of a user existing in the site with a role equal or less than your role, you will be redirected to the user's management page (admin can access all roles, manager can access manager, guests, installers).
When pressing on a log of a user existing in the site with a higher role than yours, a modal popup will show the user profile picture, full name and email address.
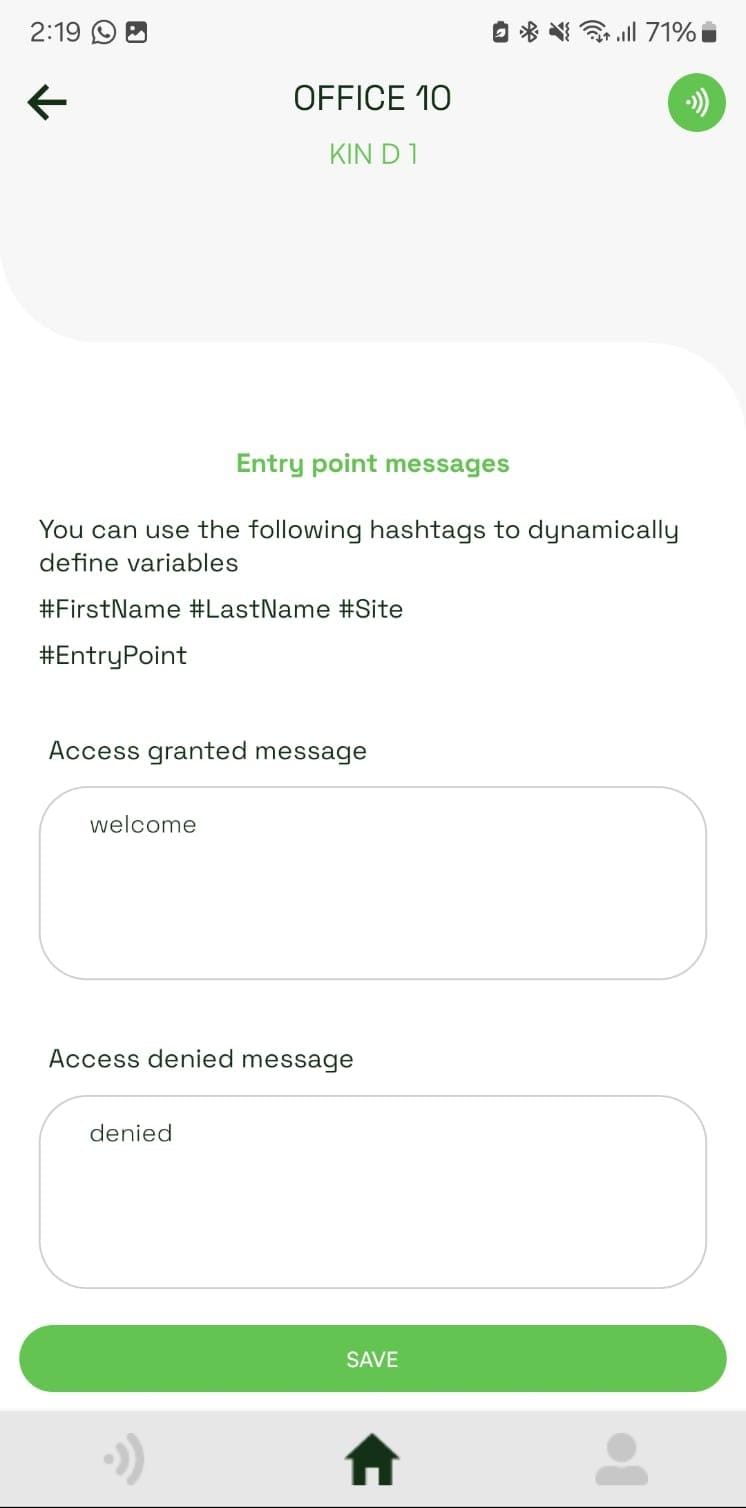
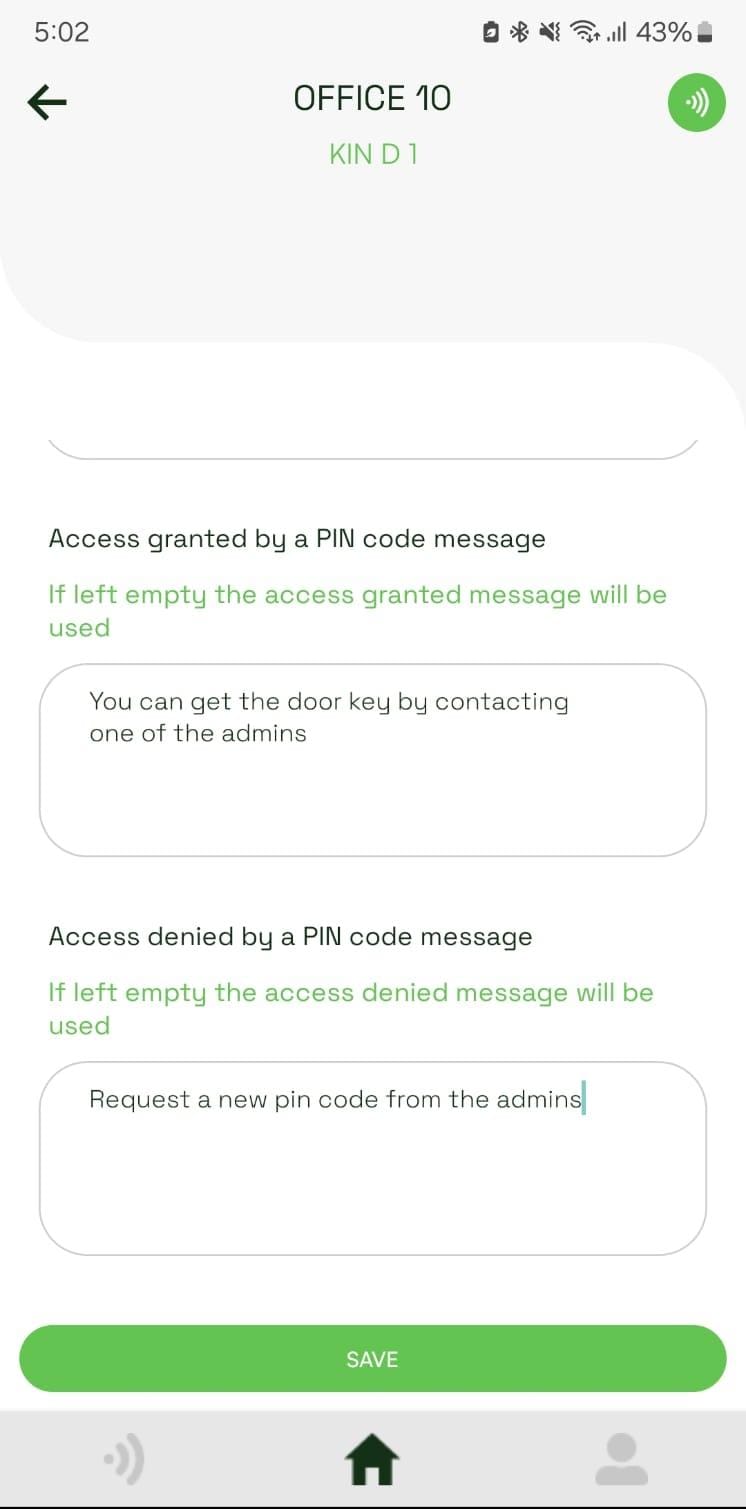
In the entry point settings, if the entry point contractor access is turned on, two new messages can be defined: Access granted by a PIN code message and Access denied by a PIN code message. If these inputs are left empty the entry point granted and denied messages will be used by default.
▼v.5.3.6
14-05-2025Introduction of new KIN hardware to the app
Compatibility with KIN S W01, KIN S B01, Controller 2.0, KIN H
Performance optimization
Bug fixing
▼v.5.3.5
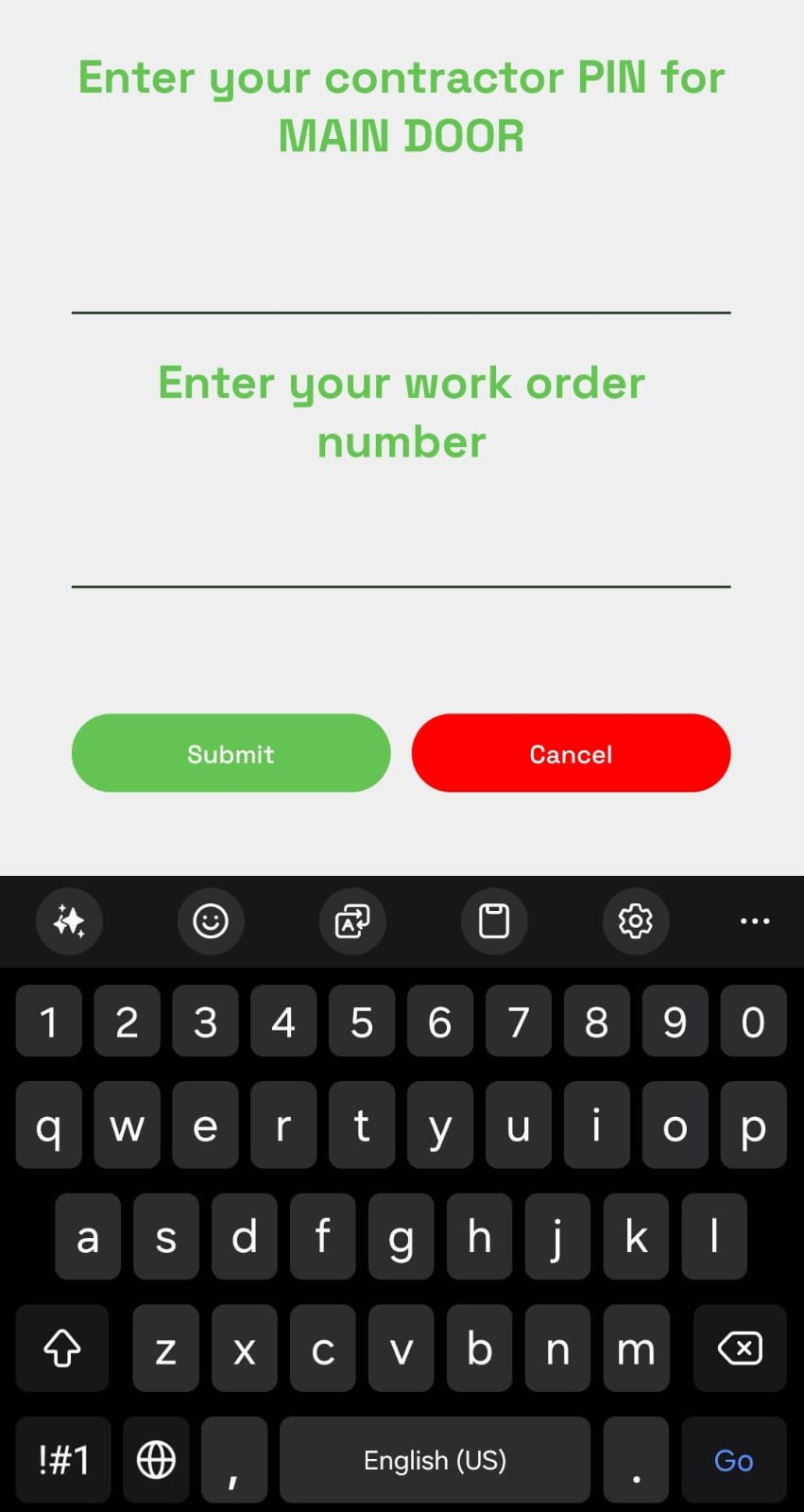
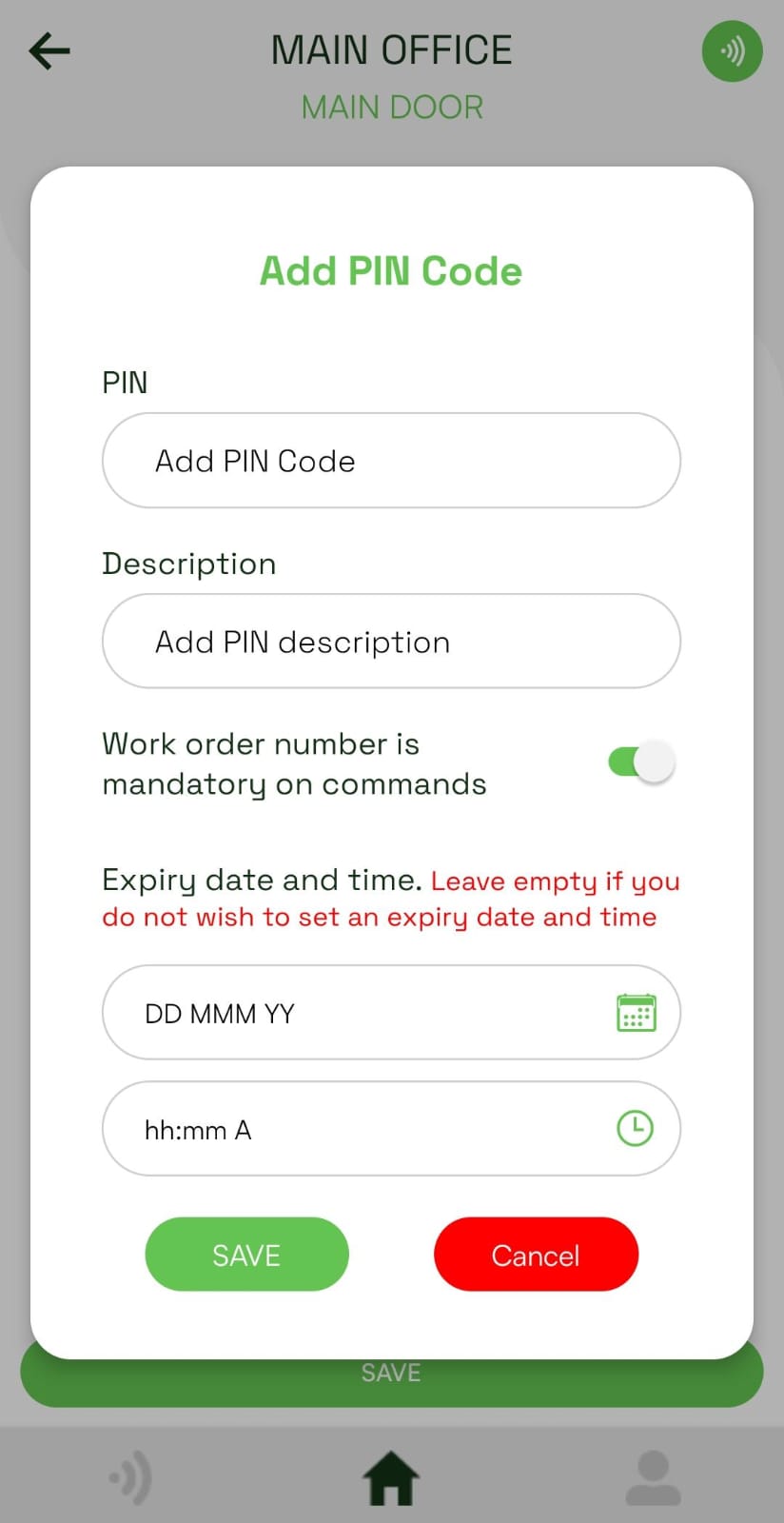
11-05-2024When issuing a command to a KIN with a PIN code, the user is able to enter a work order number
The ability to set the work order number as mandatory on selected PIN codes
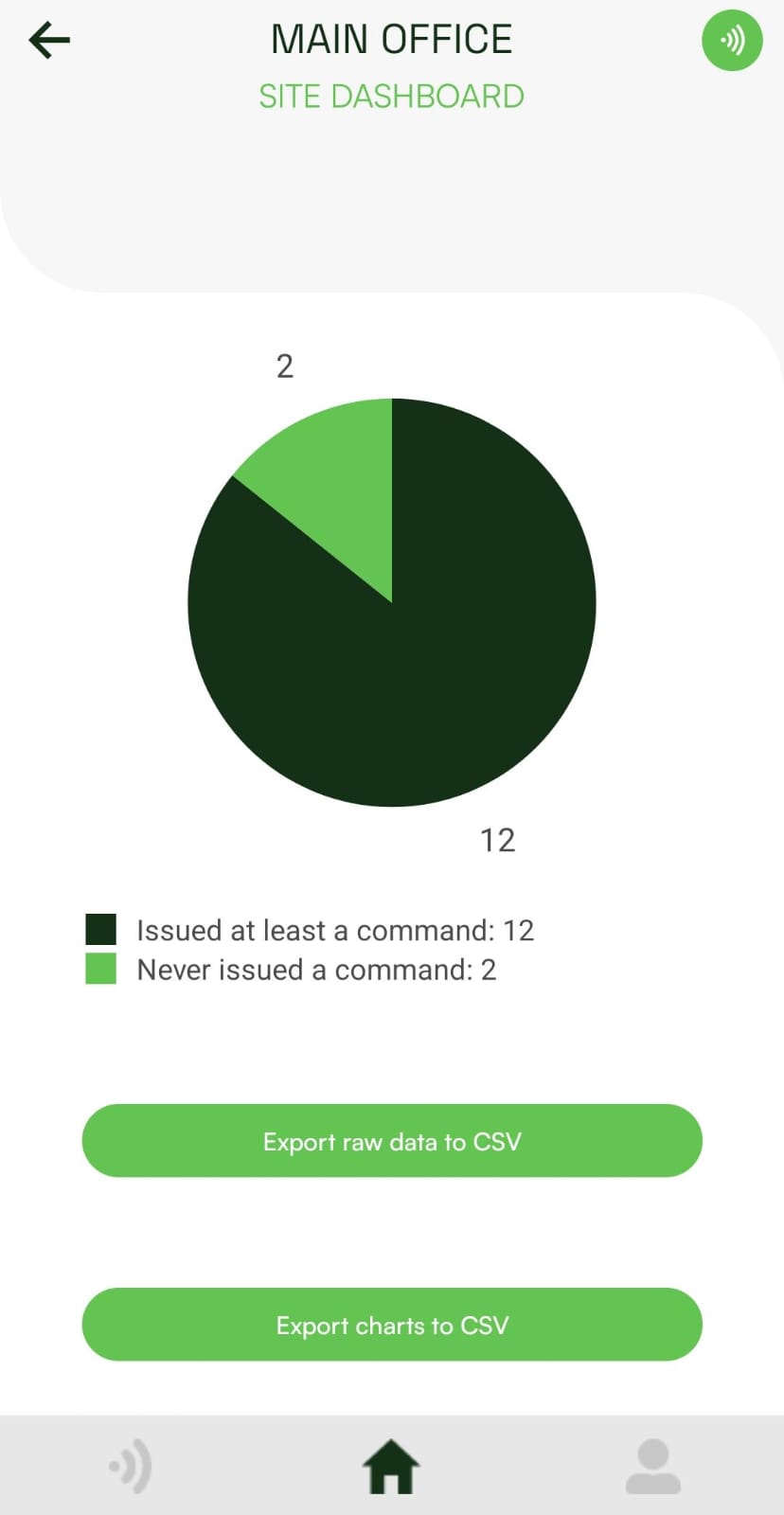
The ability to export raw data in the site dashboard
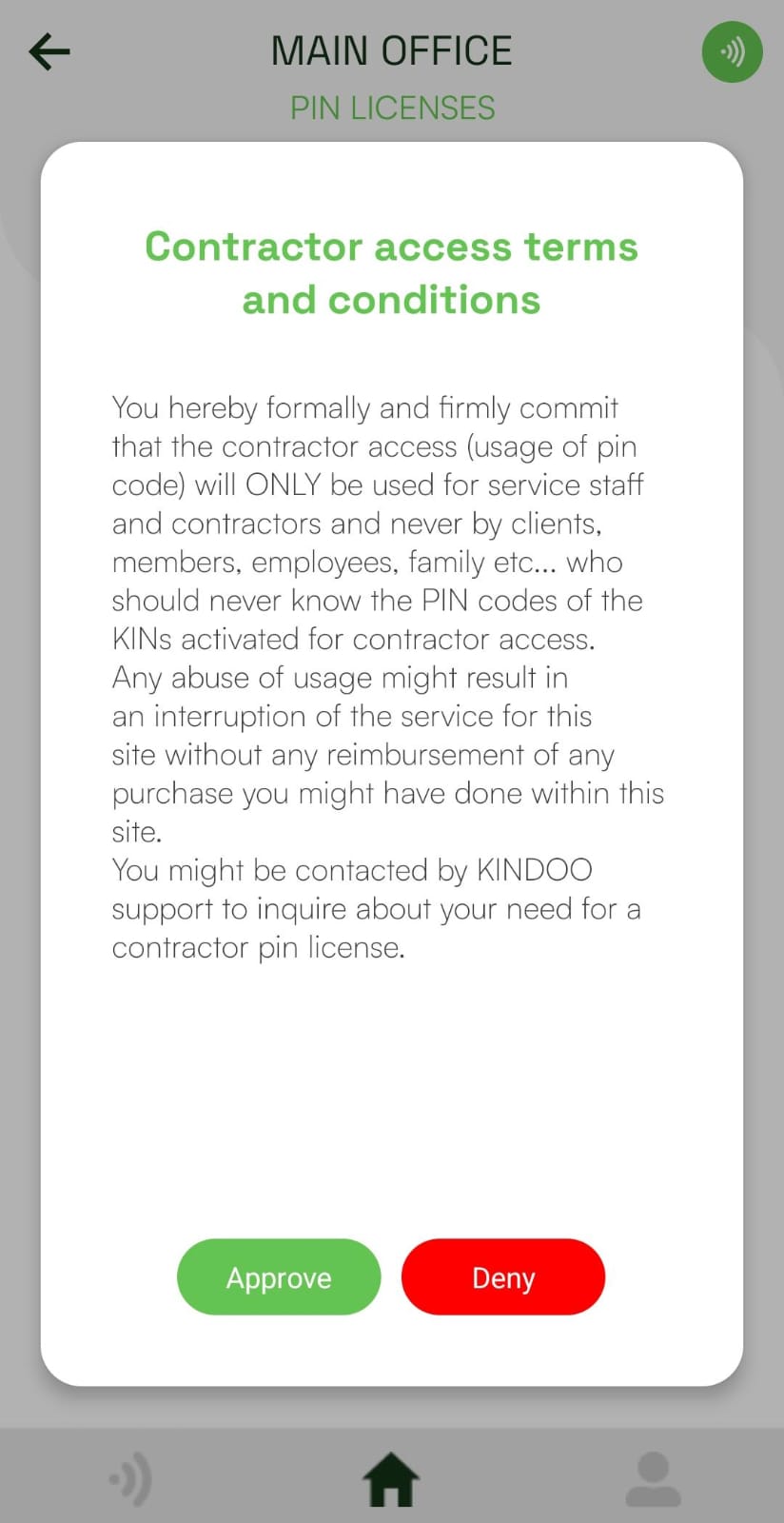
Contractor access terms and conditions must be accepted when purchasing PIN license
Contractor access terms and conditions must be accepted when turning on the contractor access on a KIN